In today’s digital landscape, data breaches have become alarmingly common, threatening businesses of all sizes. At Project IT, we’ve witnessed firsthand the devastating consequences of inadequate data protection measures.
Data encryption stands as a powerful shield against these threats, safeguarding sensitive information from unauthorised access. This blog post explores why encryption is no longer optional but essential for modern businesses to thrive and maintain trust in an increasingly interconnected world.
The Escalating Cyber Threat Landscape
The Alarming Rise of Cyber Incidents
The digital realm has transformed into a battleground, with cyber threats evolving at an unprecedented pace. The frequency and sophistication of cyberattacks targeting businesses of all sizes have skyrocketed in recent years.
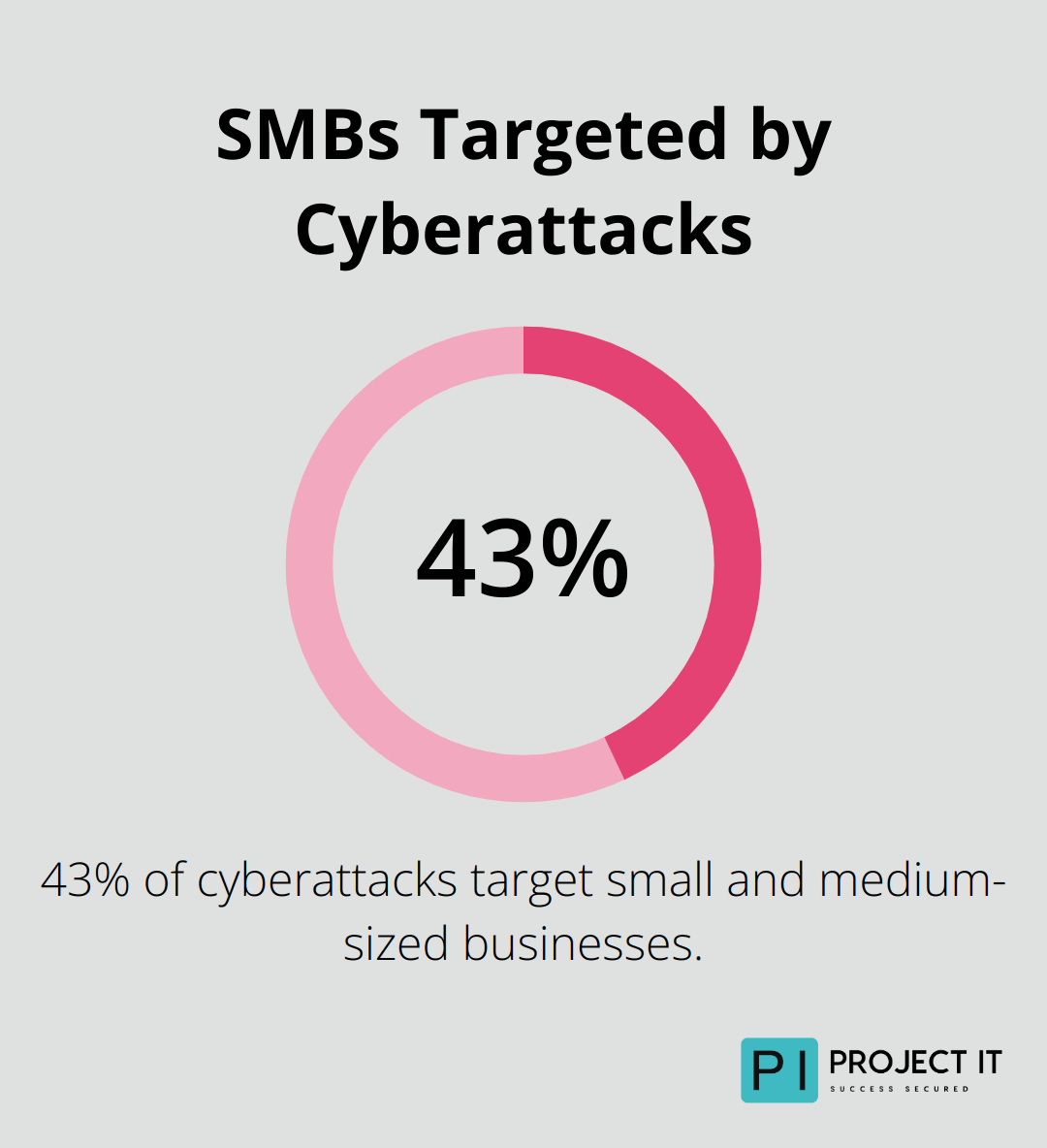
In 2023, data breaches reached an all-time high. IBM’s Cost of a Data Breach Report 2025 provides up-to-date insights into cybersecurity threats and their financial impacts on organisations. Small and medium-sized businesses face particular vulnerability, with 43% of cyberattacks targeting these organisations.
Financial and Reputational Fallout
The repercussions of a data breach extend far beyond immediate financial losses. Companies face steep fines for non-compliance with data protection regulations. Under GDPR, for instance, organisations risk fines of up to €20 million (or 4% of their global annual turnover, whichever is higher).
Reputational damage often proves even more devastating. A Ponemon Institute study found that 65% of consumers lost trust in organisations that experienced a data breach. This erosion of trust frequently translates to customer churn and decreased revenue.
The Evolution of Hacking Techniques
Cybercriminals continuously refine their methods. Ransomware attacks have seen a significant increase in recent years. These attacks have become more targeted and sophisticated, often combining multiple techniques to bypass traditional security measures.
AI-powered attacks represent another growing concern. Hackers now leverage machine learning algorithms to automate attacks and evade detection. This trend underscores the necessity for businesses to adopt equally advanced security measures.
Actionable Steps to Enhance Security
- Implement Multi-Factor Authentication (MFA): MFA prevents 99.9% of account compromise attacks. Make it mandatory across all systems.
- Conduct Regular Security Audits: Perform comprehensive security assessments at least quarterly to identify and address vulnerabilities.
- Prioritise Employee Training: Invest in ongoing cybersecurity awareness training. Human error remains a leading cause of data breaches.
- Develop an Incident Response Plan: Create and regularly test a robust incident response plan to minimise damage in case of a breach.
- Deploy Advanced Threat Detection: Implement AI-powered security tools that detect and respond to threats in real-time.
The current threat landscape demands immediate action. Businesses must prioritise cybersecurity to protect their assets, reputation, and customer trust. As we move forward, it’s clear that data encryption plays a pivotal role in this defence strategy. Let’s explore why encryption has become non-negotiable for modern businesses in our increasingly interconnected world.
Why Data Encryption Is Essential for Your Business
Fortifying Your Most Valuable Assets
Data encryption transforms your sensitive information into an unreadable format, creating an impenetrable barrier against unauthorised access. This protection extends to customer data, financial records, and proprietary information (your company’s crown jewels).
A study by IBM revealed that encryption can reduce the cost of a data breach by approximately $360,000. This substantial saving highlights the tangible benefits of implementing robust encryption practices.
Navigating Regulatory Compliance
Data protection regulations (such as GDPR, HIPAA, and PCI DSS) mandate encryption for specific types of data. Non-compliance can result in severe penalties. GDPR fines, for instance, can reach up to 4% of a company’s global annual turnover.
Encryption adoption demonstrates a proactive stance towards data protection. This approach streamlines audits and minimises the risk of regulatory penalties, positioning your company as a responsible steward of sensitive information.
Cultivating Customer Trust
In an era where data breaches dominate headlines, customers exercise caution about sharing their information. Encryption serves as a powerful trust signal, demonstrating your commitment to privacy.
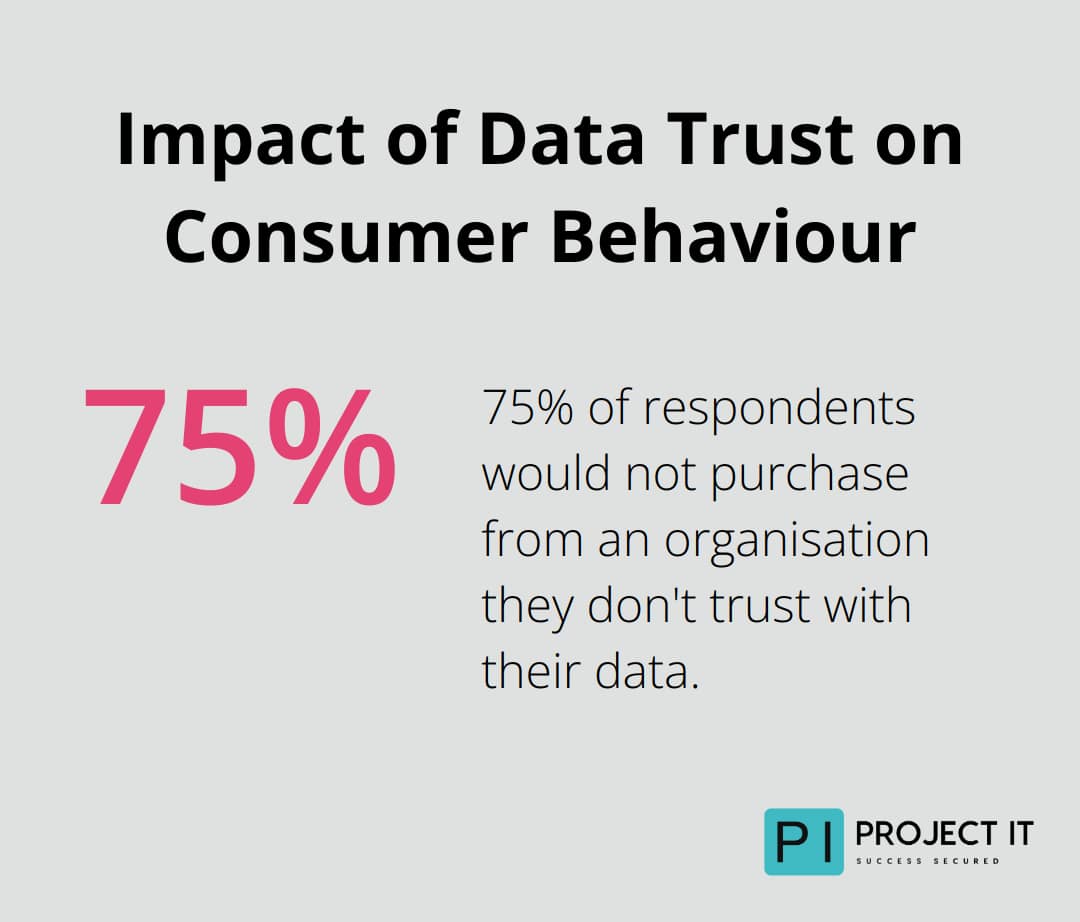
A Cisco survey found that 75% of respondents said they would not purchase from an organisation they do not trust with their data. Prioritising encryption nurtures customer relationships and fosters loyalty, transforming data protection into a competitive advantage.
Safeguarding Intellectual Property
Encryption plays a vital role in protecting your company’s intellectual property (IP). Trade secrets, product designs, and research data represent significant investments and competitive advantages. Robust encryption ensures this valuable information remains secure from industrial espionage and cyber threats.
Enabling Secure Remote Work
The shift towards remote and hybrid work environments has expanded the attack surface for many organisations. Encryption (particularly for data in transit) allows employees to access company resources securely from any location. This flexibility enhances productivity without compromising security.
Data encryption transcends mere technical implementation; it represents a strategic asset that protects your most valuable information and builds stakeholder trust. As cyber threats continue to evolve, encryption will play an increasingly critical role in your overall security strategy. Let’s explore how to implement robust encryption measures effectively in your organisation.
How to Implement Robust Encryption
At Project IT, we understand the critical importance of proper encryption implementation. Let’s explore practical strategies for deploying strong encryption across your organisation.
Selecting Appropriate Encryption Methods
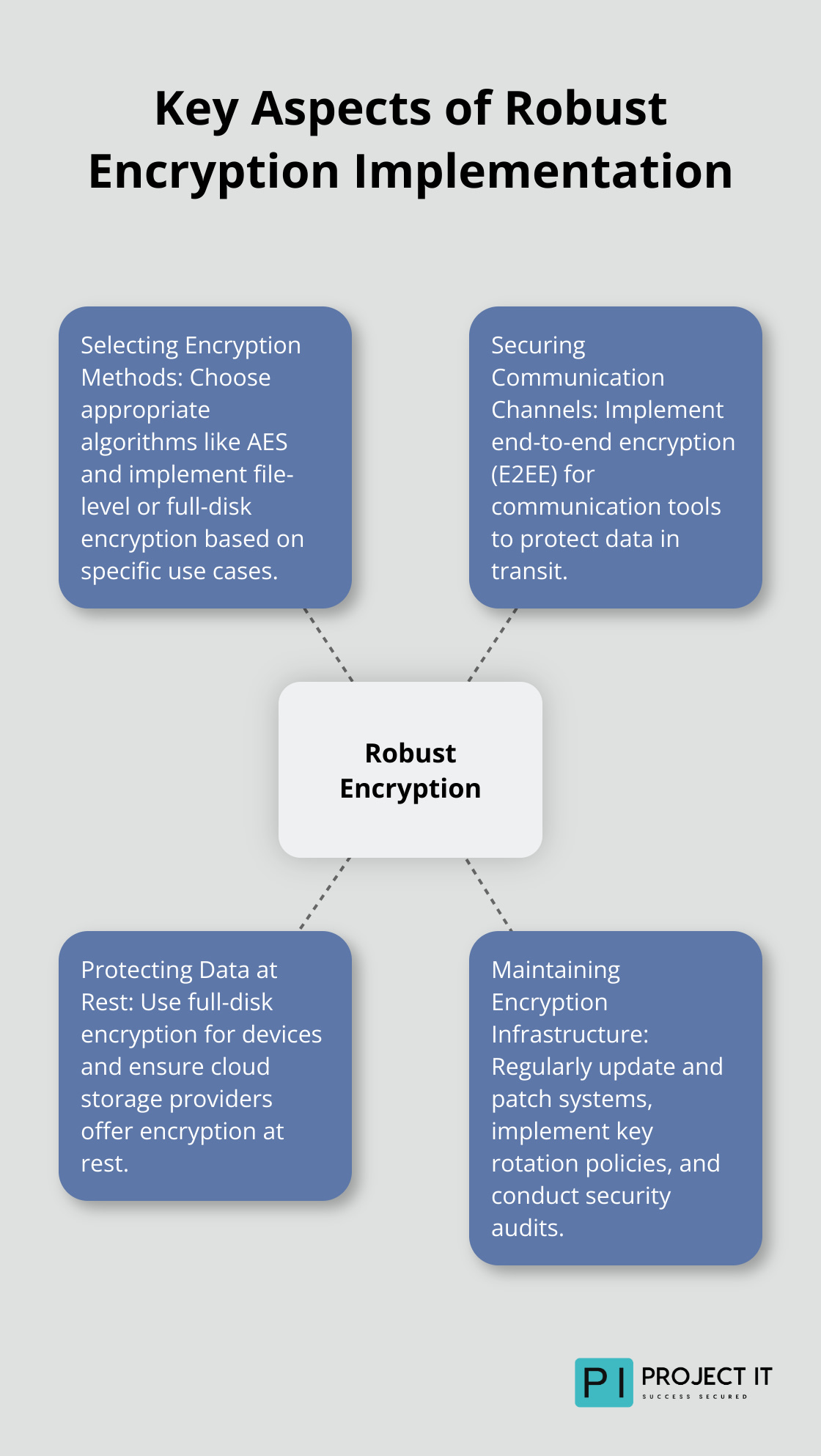
The cornerstone of any solid encryption strategy is the selection of suitable algorithms and key lengths. We recommend AES for symmetric encryption. The Advanced Encryption Standard (AES) is trusted as the standard by the U.S. Government and numerous organisations.
Consider your specific use cases when implementing encryption. File-level encryption protects individual documents effectively, while full-disk encryption safeguards entire drives. For databases, column-level encryption allows for granular protection of sensitive fields.
Securing Communication Channels
End-to-end encryption (E2EE) protects data in transit. We help clients implement E2EE for their communication tools, which significantly reduces the risk of man-in-the-middle attacks.
For email, solutions like ProtonMail or Tutanota offer built-in E2EE. Signal provides robust E2EE for both personal and business messaging. When developing custom applications, libraries such as libsodium simplify E2EE implementation.
Protecting Data at Rest
Encryption for data at rest serves as your last line of defence against physical theft or unauthorised access. We always recommend full-disk encryption for all devices (especially laptops and mobile phones that may leave the office).
For cloud storage, verify that your provider offers encryption at rest. Most major cloud platforms (AWS, Azure, and Google Cloud) provide this by default, but it’s essential to confirm and configure it correctly.
Maintaining Your Encryption Infrastructure
Encryption requires ongoing attention. Regular updates and patch management address newly discovered vulnerabilities. We recommend automating this process as much as possible to ensure consistent protection.
Key management is another vital aspect. Implement a robust key rotation policy and rotate encryption keys at least annually. Use a dedicated key management system (KMS) to store and manage your encryption keys securely.
Regularly test your encryption implementation. Conduct penetration testing and security audits to identify potential weaknesses in your encryption strategy. This proactive approach helps you stay ahead of evolving threats and ensures your sensitive data remains protected.
Final Thoughts
Data encryption stands as a cornerstone of modern business security. The rising tide of cyber threats and stringent regulatory requirements make encryption an essential safeguard for organisations of all sizes. Encryption protects sensitive information and builds trust with customers, partners, and stakeholders, which translates into long-term sustainability and competitive advantage in the digital marketplace.
Encryption enables secure remote work, safeguards intellectual property, and demonstrates a commitment to data protection that resonates with privacy-conscious consumers. As cyber threats evolve, encryption will play an even more critical role in maintaining business resilience and continuity. We at Project IT understand the complexities of implementing and managing effective encryption strategies (our team of experts specialises in tailoring solutions to meet unique business needs).
Don’t wait for a data breach to highlight vulnerabilities in your security infrastructure. Take proactive steps to implement strong encryption measures across your organisation. Contact Project IT today to prioritise data encryption as a fundamental component of your overall security strategy.


