Malware threats are evolving at an alarming rate, putting businesses at risk of data breaches, financial losses, and reputational damage.
At Project IT, we’ve seen first-hand how devastating these attacks can be for organisations of all sizes.
This blog post will explore the latest malware protection strategies, including managed antivirus solutions, to help safeguard your business against these ever-changing threats.
What Are Modern Malware Threats?
The Evolving Landscape of Malware
Modern malware threats have become increasingly sophisticated, posing significant risks to businesses of all sizes. The complexity and frequency of these attacks continue to rise at an alarming rate.
Malware has evolved far beyond simple viruses. Today, we face a wide array of threats. Ransomware attacks have increased by 13% in the past five years, with each incident costing victims an average of $1.85 million (according to IBM). Trojans, worms, and spyware continue to advance, employing sophisticated evasion techniques that challenge traditional detection methods.
A particularly concerning trend is the emergence of file less malware. These threats reside in a computer’s RAM, leaving no trace on the hard drive and evading detection by conventional antivirus solutions.
The Business Impact of Malware
The consequences of a malware attack can devastate a business. IBM reports that the global average cost of a data breach in 2024 has risen to $4.88 million (a 10% increase over the previous year). However, the impact extends beyond financial losses. Reputational damage can persist long after the initial attack and prove irreparable in some cases.
Small and medium-sized businesses (SMBs) face particular vulnerability. Even more alarming, 55% of SMBs report that a financial impact of less than $50,000 could potentially shut down their operations.
New Tactics in the Malware Arsenal
Cybercriminals constantly innovate their methods. Supply chain attacks have surged, where attackers compromise trusted software providers to distribute malware to their customers. The SolarWinds breach in 2020 exemplified this tactic, affecting thousands of organisations worldwide.
Another emerging threat involves the use of artificial intelligence in malware creation. AI-powered attacks can adapt to their environment, making them more challenging to detect and neutralise. This trend underscores the need for equally advanced defence mechanisms.
The Rise of Ransomware-as-a-Service (RaaS)
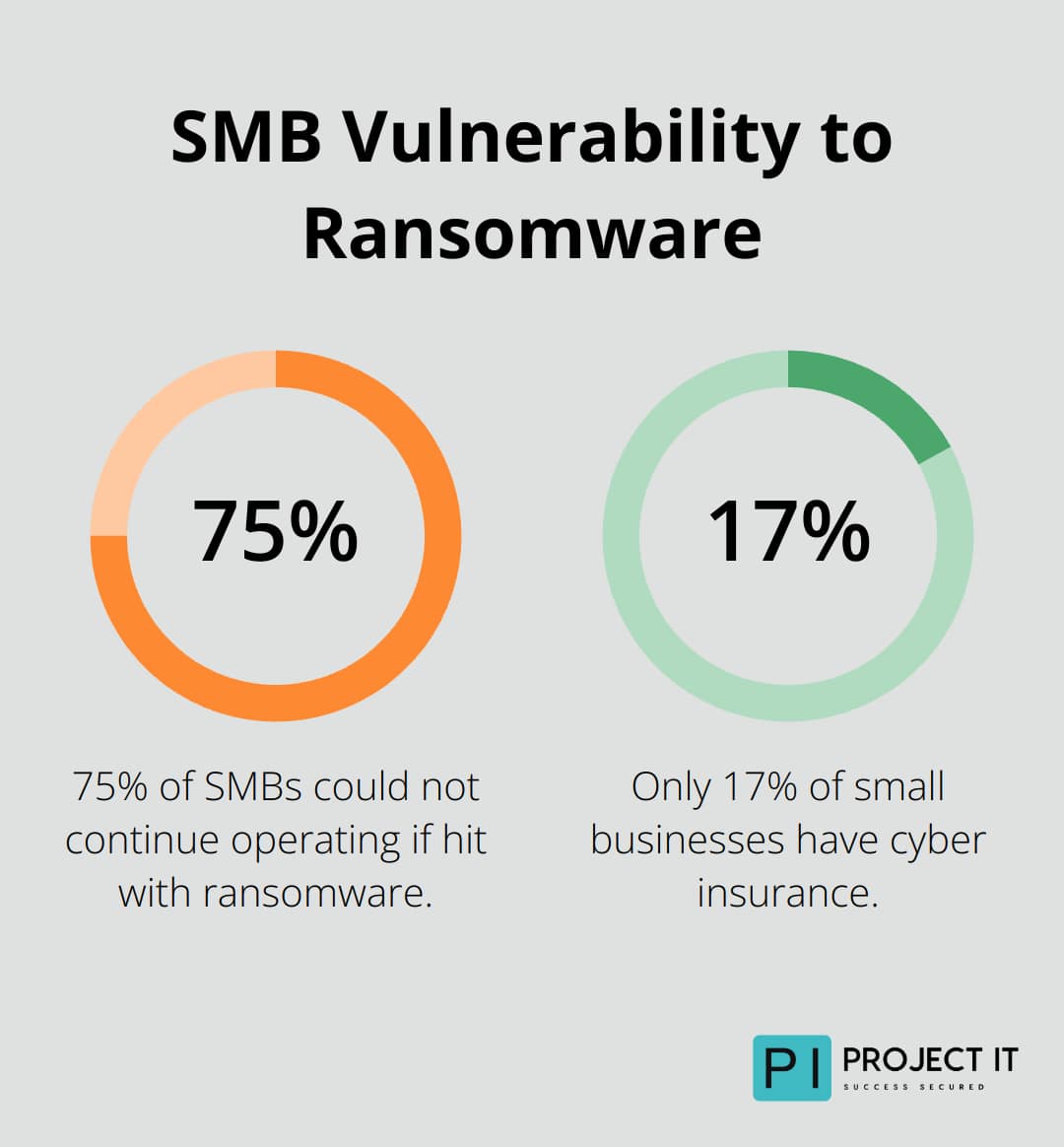
The cybercrime landscape has witnessed the emergence of Ransomware-as-a-Service (RaaS) models. This approach allows even less technically skilled criminals to launch sophisticated attacks using pre-built malware kits. Recent statistics show that 75% of SMBs could not continue operating if they were hit with ransomware, and only 17% of small businesses have cyber insurance.
IoT Vulnerabilities and Malware
As the Internet of Things (IoT) expands, so do the potential entry points for malware. Many IoT devices lack robust security measures, making them attractive targets for cybercriminals. Malware targeting IoT devices can create large-scale botnets, used for DDoS attacks or as gateways into corporate networks.
The evolving nature of malware threats necessitates a proactive and comprehensive approach to cybersecurity. In the next section, we will explore essential strategies to protect your business against these sophisticated malware threats.
How to Protect Your Business from Malware
At Project IT, we’ve witnessed the devastating impact of malware attacks on businesses. We want to share practical strategies to safeguard your company. Here are actionable steps you can take today.
Invest in Advanced Antivirus Solutions
Traditional antivirus software no longer suffices. You need comprehensive endpoint protection that detects and neutralises sophisticated threats. Look for solutions that offer real-time monitoring, behavioural analysis, and machine learning capabilities.
Microsoft Defender Advanced Threat Protection has demonstrated high-quality protection in categories such as protection, performance, and usability in recent tests. This level of protection proves essential in today’s threat landscape.
Prioritise Regular Updates
Software vulnerabilities serve as prime targets for cybercriminals. The Ponemon Institute reports that 60% of data breaches in 2024 involved unpatched vulnerabilities.
Set up automatic updates for all your systems and applications. If you use Windows, enable Windows Update for Business to manage and deploy updates across your organisation efficiently.
Educate Your Employees
Your staff forms your first line of defence. The 2024 Verizon Data Breach Investigations Report reveals that 68% of breaches involved a human element. Regular training sessions on identifying phishing emails, safe browsing habits, and proper data handling are essential.
Try implementing simulated phishing tests. Companies that run these tests report a 50% reduction in successful phishing attacks (according to a study by Infosec Institute).
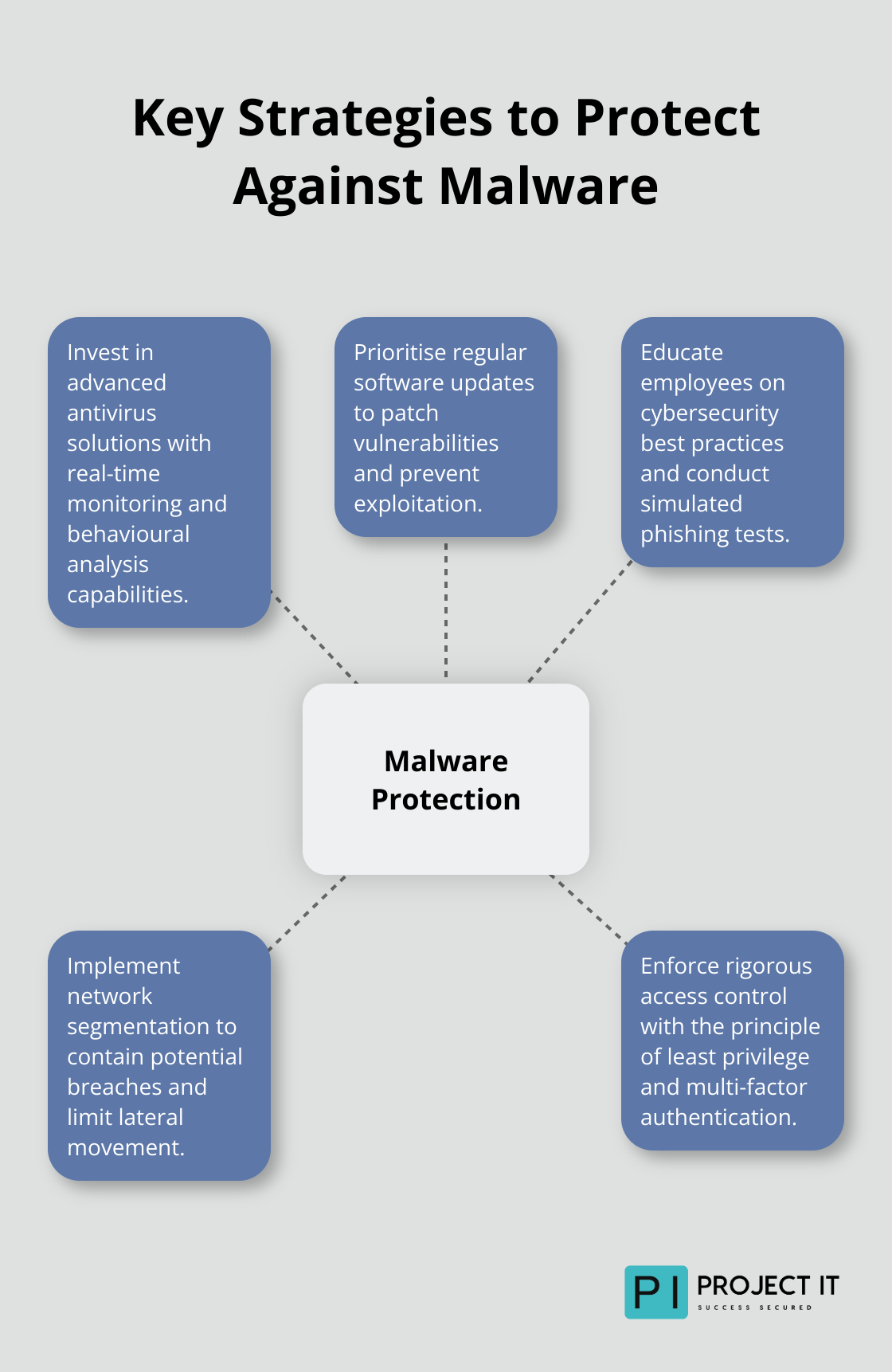
Implement Network Segmentation
Network segmentation serves as a powerful tool in your security arsenal. Divide your network into smaller, isolated segments to contain potential breaches and limit lateral movement.
Use VLANs (Virtual Local Area Networks) to separately different departments or types of data. Place firewalls between segments to control traffic flow. This approach can reduce the impact of a breach by up to 60% (according to research by Forrester).
Enforce Rigorous Access Control
The principle of least privilege should guide your access control strategy. Grant users only the minimum level of access they need to perform their jobs. Use multi-factor authentication (MFA) for all accounts, especially those with elevated privileges.
Google reports that implementing MFA can block up to 99% of automated attacks. It’s a simple yet highly effective security measure.
As the threat landscape continues to evolve, businesses must adopt a proactive stance against malware. The next section will explore advanced malware defence techniques to further fortify your organisation’s security posture.
Cutting-Edge Malware Defence
At Project IT, we have observed how traditional security measures often fail against today’s sophisticated malware. We continuously explore and implement advanced defence techniques to stay ahead of cybercriminals.
The Power of Endpoint Detection and Response (EDR)
EDR systems have revolutionised malware defence. Unlike traditional antivirus software that relies on signature-based detection, EDR monitors endpoint and network events in real-time. This approach allows for rapid detection and response to threats that might otherwise slip through the cracks.
A study by Ponemon Institute found that the average data breach cost is USD 4.45 million. Many businesses experience similar results, with EDR catching threats that traditional antivirus missed entirely.
AI-Powered Behavioural Analysis
Artificial Intelligence (AI) and Machine Learning (ML) have become game-changers in malware detection. These technologies analyse patterns and behaviours rather than relying solely on known malware signatures.
For instance, Cylance (an AI-based security solution) claims to prevent 99.1% of malware attacks. The implementation of AI-driven security tools often reduces false positives by up to 60%, allowing security teams to focus on real threats.
Sandboxing: Isolating Threats Safely
Sandboxing technology provides a secure environment to execute and analyse suspicious files or programmes without risking the main system. This approach proves particularly effective against zero-day threats and advanced persistent threats (APTs).
VMRay (a leading sandboxing solution) reports that their technology detects 30% more malware variants compared to traditional methods. The integration of sandboxing into security stacks significantly reduces the risk of malware infections from email attachments and downloaded files.

Proactive Threat Hunting
Proactive threat hunting involves actively searching for hidden threats within your network. This approach proves crucial in detecting sophisticated malware that may have evaded other security measures.
According to the SANS 2025 Threat Hunting Survey, behavioural threat hunting can do what AI and IOC-hunts can’t do alone. Threat hunting teams often uncover numerous latent threats in client networks, often before they cause any damage.
The implementation of these advanced techniques requires expertise and resources that many businesses lack internally. Managed security services provide a solution. A partnership with a provider like Project IT grants access to cutting-edge malware defence without the overhead of building and maintaining an in-house security team.
A multi-layered approach proves key to effective malware defence. While these advanced techniques are powerful, they work best when combined with fundamental strategies. Vigilance, system updates, and expert help when needed form the foundation of a robust defence against modern malware threats.
Final Thoughts
The battle against malware threats requires a comprehensive, multi-layered approach. Essential strategies include robust antivirus solutions, regular software updates, employee training, and network segmentation. Advanced techniques such as Endpoint Detection and Response (EDR) systems, AI-powered analysis, sandboxing, and proactive threat hunting provide the agility needed to combat today’s complex threats.
Ongoing vigilance is essential as the threat landscape constantly shifts. Staying informed about emerging threats and regularly reassessing security measures will maintain a robust defence posture. Managed antivirus services offer access to expertise and advanced technologies without extensive in-house resources.
Project IT specialises in delivering comprehensive managed IT services, including state-of-the-art security solutions tailored to your business needs. Effective malware protection is an ongoing process that requires proactive measures, advanced technologies, and partnerships with experienced professionals to enhance your business’s resilience against malware threats.


