Network security is more critical than ever in today’s digital landscape. With cyber threats evolving rapidly, many companies are unknowingly exposed to significant risks.
At Project IT, we’ve seen firsthand how vulnerable networks can compromise entire organisations. This post will explore common security weaknesses, essential protective measures, and advanced strategies to fortify your company’s digital defences.
Network Vulnerabilities You Can’t Ignore
At Project IT, we’ve witnessed numerous businesses fall victim to preventable security breaches. Let’s explore the most common network vulnerabilities that could put your company at risk right now.
The Danger of Outdated Systems
Outdated software and operating systems leave your network exposed. The average cost of a data breach was $4.88 million in 2024, the highest average on record. Cybercriminals actively seek out these vulnerabilities. The WannaCry ransomware attack in 2017 primarily targeted systems that hadn’t applied a critical Windows update.
Action step: Conduct a thorough inventory of all your software and systems. Set up automatic updates where possible, and create a schedule for manual updates.
The Password Predicament
Weak passwords provide easy access for hackers. Despite years of warnings, “123456” and “password” still top the lists of most common passwords. Even worse, 65% of people reuse passwords across multiple accounts. This means a breach in one system could compromise all your company’s accounts.
Action step: Implement a password manager across your organisation. Require complex passwords (at least 12 characters), and enforce regular password changes.
The Wi-Fi Vulnerability
Unsecured Wi-Fi networks offer a goldmine for cybercriminals. A 2022 survey revealed that 79% of public Wi-Fi users took no action to protect their data. Even within office buildings, poorly secured networks can allow neighbouring businesses or visitors to access sensitive information.
Action step: Secure your Wi-Fi with WPA3 encryption, hide your SSID, and use a strong, unique password. For employees working remotely, provide a VPN solution.
The Human Element
Employee security awareness (or lack thereof) remains perhaps the most significant vulnerability. The human element was involved in 82% of breaches, and consists of Social attacks, Error and Misuse. Phishing attacks, in particular, rely on tricking employees into revealing sensitive information or clicking malicious links.
Action step: Implement regular, engaging security awareness training for all employees. Include simulated phishing tests to keep staff vigilant.

These vulnerabilities represent just the tip of the iceberg when it comes to network security risks. In the next section, we’ll explore essential measures to further fortify your defences and create a robust security posture for your organisation.
How to Fortify Your Network Defences
At Project IT, we have witnessed the dramatic impact of robust security measures on an organisation’s risk profile. Let’s explore essential strategies to strengthen your network defences.
Firewalls and Intrusion Detection: Your First Line of Defence
Modern firewalls and intrusion detection systems (IDS) protect your network. Next-generation firewalls (NGFW) offer advanced features like application awareness and integrated intrusion prevention. Gartner predicts that by 2025, 70% of new firewall deployments will be NGFWs.
We recommend a layered approach. Start with a robust perimeter firewall, then add internal firewalls to segment your network. This limits the spread of potential breaches. For intrusion detection, consider both network-based and host-based IDS to catch threats at multiple levels.
The Power of Regular Security Audits
Security requires constant vigilance. Regular audits and penetration testing identify vulnerabilities before attackers do. Research indicates that encryption is incredibly effective, lowering data breach costs by an average of $360,000.
Try to schedule quarterly vulnerability scans and annual penetration tests. These should cover both external and internal systems. Don’t overlook physical security audits – many breaches start with unauthorised physical access.
Multi-Factor Authentication: A Simple Yet Powerful Tool
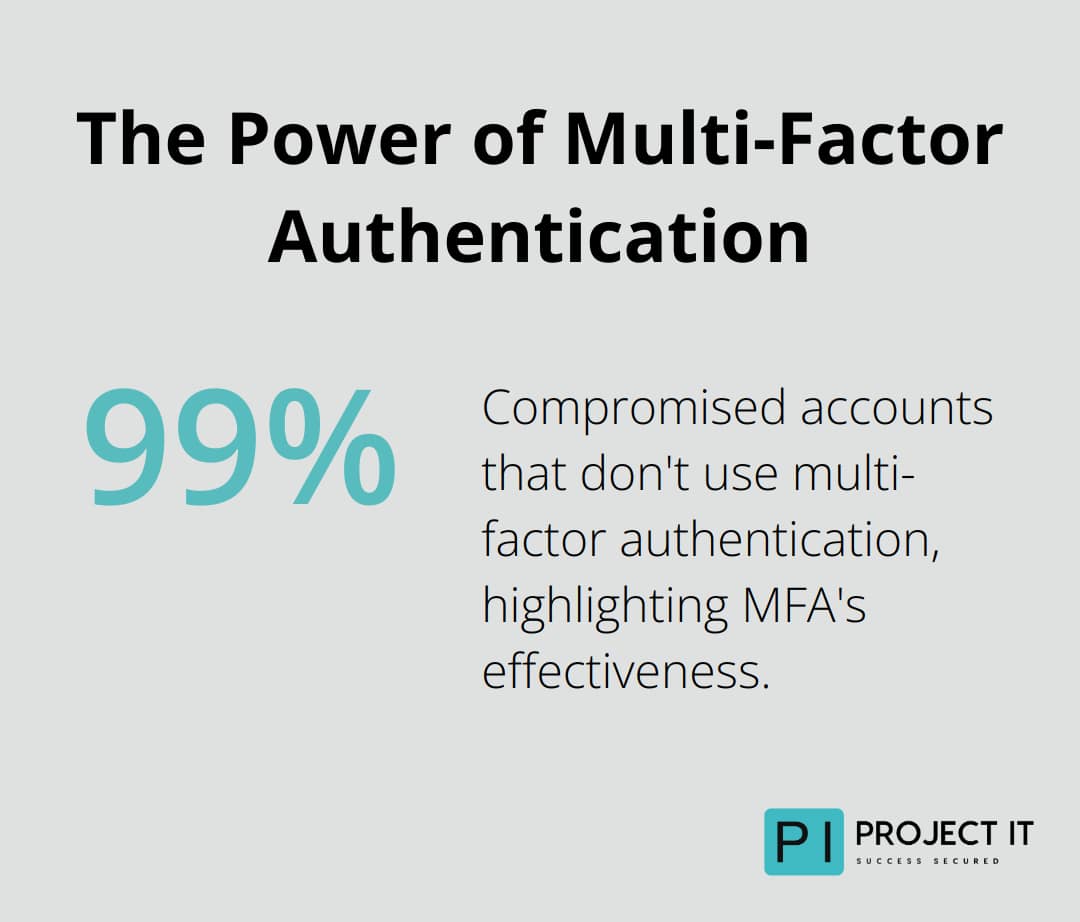
Multi-factor authentication (MFA) is one of the most cost-effective security measures you can implement. More than 99.9% of compromised accounts don’t have MFA, which leaves them vulnerable to password spray, phishing, and password reuse.
Implement MFA across all critical systems and user accounts (including email, VPNs, and any systems containing sensitive data). For the best security, combine something the user knows (password), has (smartphone), and is (biometrics).
Empowering Your Employees Through Training
Your employees are both your greatest asset and your biggest potential vulnerability. A well-trained workforce can be your most effective defence against phishing and social engineering attacks.
Implement a comprehensive, ongoing security awareness program. This should include:
- Regular phishing simulations to test and train employees
- Workshops on identifying and reporting suspicious activities
- Clear policies on data handling and device usage
Make training engaging and relevant. Use real-world examples and tailor content to different departments. The key is to foster a culture of security awareness throughout your organisation.
These measures form the foundation of a robust security strategy. As threats evolve, your defences must adapt. The next section will explore advanced strategies to take your network security to new heights.
Cutting-Edge Security Strategies for Modern Networks
At Project IT, we constantly evolve our security strategies to stay ahead of emerging threats. Let’s explore some advanced techniques that can significantly enhance your network’s defences.
Zero Trust: Trust Nothing, Verify Everything
The Zero Trust model revolutionises network security. Unlike traditional perimeter-based security, Zero Trust assumes no user or device is trustworthy by default, even if they’re inside the network.
Zero Trust implementation involves:
- Strict identity verification for every person and device trying to access resources on the network.
- Limiting access to only what’s necessary (principle of least privilege).
- Inspection and logging of all traffic.
AI-Powered Threat Detection: Staying One Step Ahead
Artificial Intelligence (AI) and Machine Learning (ML) are game-changers in cybersecurity. These technologies analyse vast amounts of data to detect anomalies and potential threats faster than any human could.
To leverage AI in your security strategy:
- Implement AI-powered Security Information and Event Management (SIEM) systems.
- Use ML algorithms to establish baseline network behaviour and flag deviations.
- Employ AI for automated threat response to reduce reaction times.
SASE: Securing the Cloud-First, Mobile-First World
Secure Access Service Edge (SASE) is a cloud-based security model that combines network security functions with WAN capabilities. It’s particularly effective for businesses with remote workers and cloud-based resources.
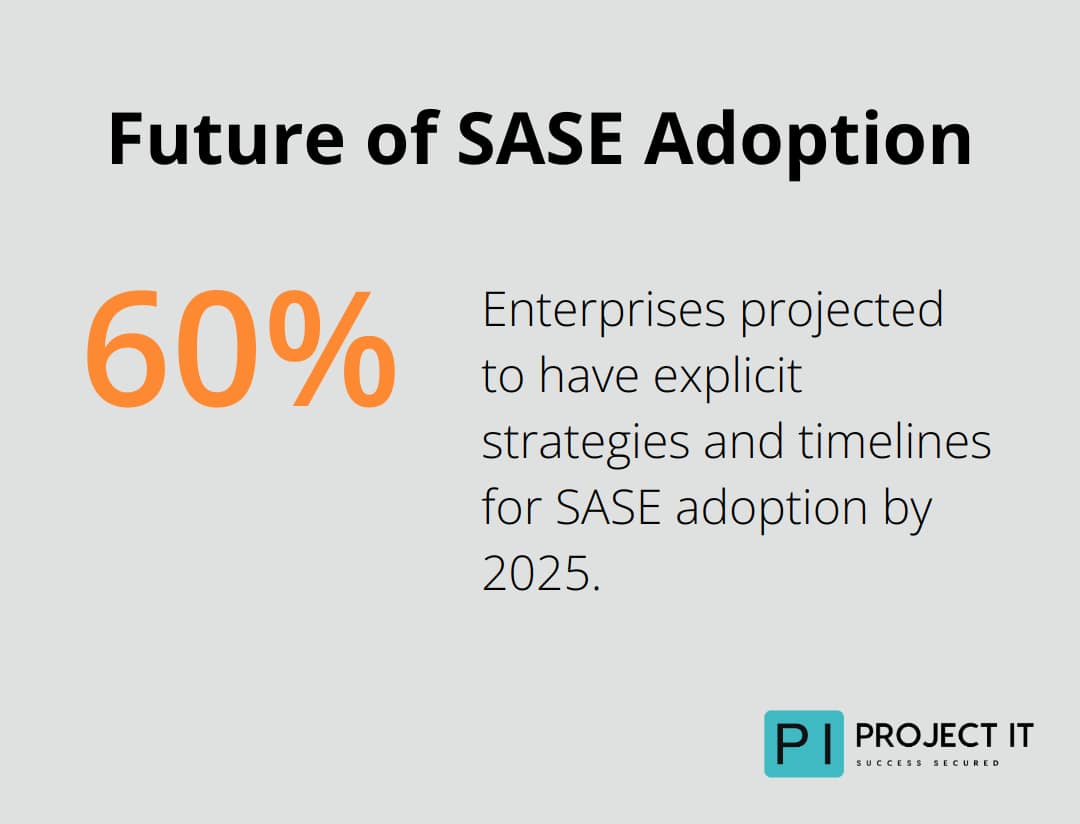
Experts forecast that by 2025, at least 60% of enterprises will have explicit strategies and timelines for SASE adoption.
Key components of SASE include:
- SD-WAN capabilities
- Cloud Access Security Broker (CASB)
- Firewall-as-a-Service (FWaaS)
- Zero Trust Network Access (ZTNA)
Continuous Network Monitoring: The 24/7 Guard
In today’s threat landscape, point-in-time security checks no longer suffice. Continuous network monitoring provides real-time visibility into your network’s security posture.
Effective continuous monitoring involves:
- Real-time log analysis
- Network traffic analysis
- Endpoint monitoring
- Automated alerting systems
These advanced strategies can transform an organisation’s security posture. While they require investment and expertise to implement, the protection they provide is invaluable in today’s threat landscape.
Final Thoughts
Network security demands continuous vigilance and adaptation. The strategies we explored form a comprehensive approach to protect your company’s digital assets. Strong security practices can become a competitive advantage, demonstrating to clients and partners that you prioritise their data protection.
We recommend you assess your current vulnerabilities and implement essential measures such as strong firewalls, regular audits, and employee training. Advanced strategies like Zero Trust and AI-powered threat detection can further enhance your security posture. These steps will reduce the risk of data breaches, ensure business continuity, and improve operational efficiency.
You don’t have to navigate this complex landscape alone. At Project IT, we provide tailored IT solutions, including comprehensive network security services. Our team of experts can help you develop and implement a robust security strategy that aligns with your business goals and protects against evolving threats (while supporting your future growth).


