Remote work has become the new normal for many New Zealand businesses. With this shift comes a host of cybersecurity challenges that can put sensitive data at risk.
At Project IT, we’ve seen firsthand how crucial it is for companies to adapt their security measures to protect their remote workforce. This blog post will guide you through the essential steps to safeguard your remote team and maintain compliance with New Zealand’s privacy laws.
Why Remote Work in New Zealand Poses Unique Security Risks
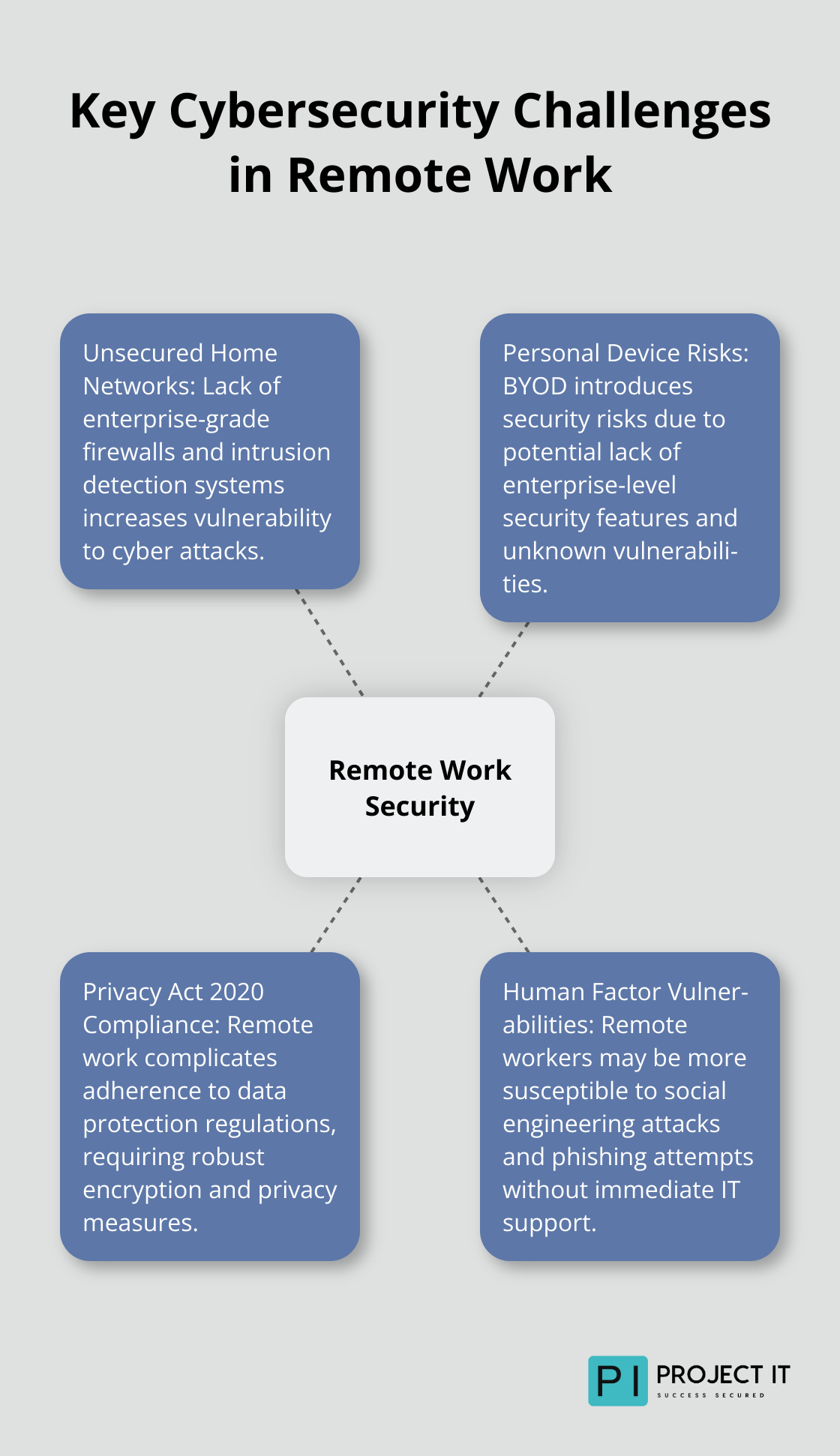
Remote work has transformed the business landscape in New Zealand, but it comes with significant challenges. The cybersecurity threats targeting remote workers have increased dramatically. Let’s explore the specific vulnerabilities of remote work environments and their implications for your business.
The Home Network Dilemma
Home networks often represent the weakest link in remote work security. Unlike office environments with enterprise-grade firewalls and intrusion detection systems, home networks typically rely on basic router security. This leaves remote workers more exposed to cyber attacks.
The National Cyber Security Centre (NCSC) provides insight into the scope and nature of cyber threats targeting the information and systems of New Zealand organisations and individuals. To mitigate this risk, companies should implement network segmentation and provide employees with secure, company-managed routers.
Personal Devices: A Double-Edged Sword
The use of personal devices for work (known as Bring Your Own Device or BYOD) is common in remote work setups. While convenient, it introduces significant security risks. Personal devices often lack enterprise-level security features and may contain malware or vulnerabilities unknown to the user.
To address this, businesses should consider providing company-managed devices or implement strict BYOD policies that include regular security audits and remote management capabilities.
Navigating the Privacy Act 2020
Compliance with the Privacy Act 2020 adds another layer of complexity to remote work security. Employers must comply with the Privacy Act 2020 and Privacy Principles, which govern how they can collect, store, use and share employee-related information.
To stay compliant, businesses must implement end-to-end encryption for data in transit and at rest, conduct regular privacy impact assessments, and provide comprehensive training on data handling procedures for remote workers.
The Human Factor in Remote Security
The human element plays a critical role in remote work security. Employees working from home may be more susceptible to social engineering attacks, phishing attempts, and other forms of manipulation. Without the immediate support of an IT team, remote workers might make security decisions that compromise company data.
Training and awareness programmes are essential to address this vulnerability. Regular (at least quarterly) security briefings, simulated phishing exercises, and clear communication channels for reporting suspicious activities can significantly reduce the risk of human error in remote work environments.
As we move forward, it’s clear that securing a remote workforce requires a multi-faceted approach. In the next section, we’ll explore the essential security measures that every New Zealand business should implement to protect their remote workers effectively. This includes effective data backup strategies to ensure data safety and security in remote work settings.
How to Fortify Your Remote Workforce
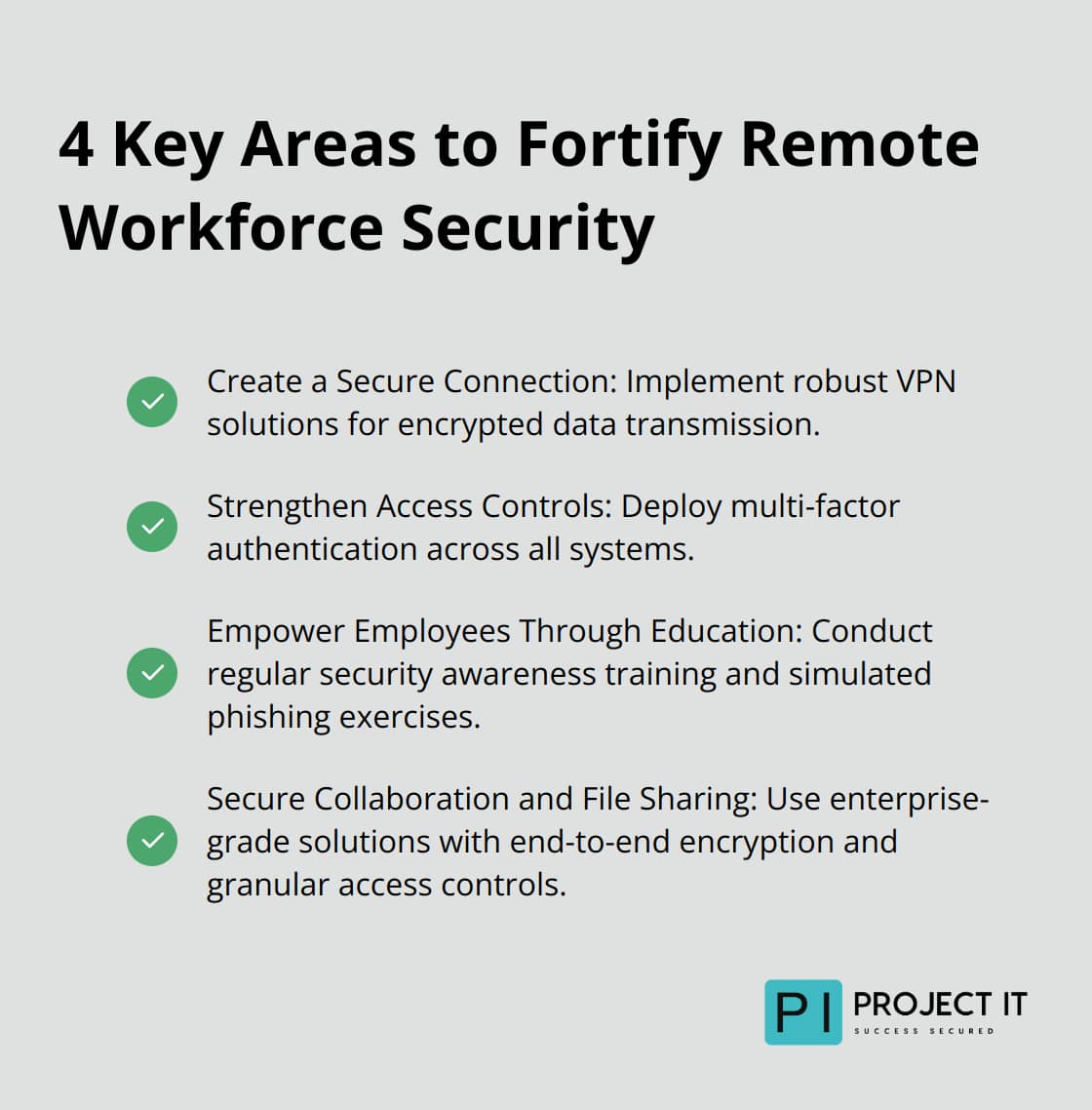
At Project IT, we have developed a comprehensive approach to secure remote workforces in New Zealand. Our strategy focuses on four key areas that significantly reduce the risk of cyber attacks and data breaches when implemented correctly.
Create a Secure Connection
The foundation of remote workforce security is a robust Virtual Private Network (VPN). A VPN encrypts all data transmitted between your employees’ devices and your company’s network, making it nearly impossible for cybercriminals to intercept sensitive information.
We recommend enterprise-grade VPN solutions that offer features like split-tunneling and automatic connection. This ensures that all work-related traffic routes through the secure VPN, while personal browsing remains separate.
Strengthen Access Controls
Multi-factor authentication (MFA) is no longer optional – it’s a necessity. MFA requires at least two forms of identification before granting access to company resources, which prevents unauthorised access even if passwords are compromised.
Implementing MFA across all systems (including email accounts, cloud storage, and other applications) reduces the risk of account takeovers. Modern MFA solutions can use biometrics, push notifications, or hardware tokens for a seamless user experience.
Empower Employees Through Education
Regular security awareness training builds a human firewall. Companies that conduct regular security training experience fewer successful phishing attacks compared to those who don’t.
Effective training programmes cover topics like identifying phishing emails, safe browsing habits, and proper handling of sensitive data. Simulated phishing exercises test and reinforce learned behaviours. Your employees are your first line of defence against cyber threats.
Secure Collaboration and File Sharing
Remote work has increased the need for secure file sharing and collaboration tools. We recommend enterprise-grade solutions that offer end-to-end encryption, granular access controls, and detailed audit logs.
Tools like Microsoft SharePoint or Google Workspace (when properly configured) provide a secure environment for document collaboration. Implementing these secure collaboration platforms can help reduce data leakage incidents.
Every business has unique needs. A team of experts can help you implement these essential security measures, tailored to your specific requirements. A comprehensive security strategy protects your remote workforce without hindering productivity.
The next chapter will explore best practices for remote device management, an essential component of a robust remote work security strategy.
Mastering Remote Device Management
At Project IT, we see how proper device management impacts remote work setups. We’ll explore practical steps to secure and manage your remote workforce’s devices effectively.
Implement Mobile Device Management (MDM)
MDM solutions form the foundation of remote device security. They allow you to monitor, manage, and secure employees’ mobile devices remotely. We recommend Microsoft Intune or VMware Workspace ONE for comprehensive device management.
With an MDM solution, you can:
- Enforce device encryption
- Install and update security software
- Configure Wi-Fi and VPN settings
- Track device location
- Remotely lock or wipe lost or stolen devices
MDM solutions can lead to a 50% reduction in mobile-related security incidents, streamline compliance audits through centralised reporting, and improve employee productivity with secure access to resources.

Establish a Robust Password Policy
Weak passwords invite hackers. Implement a password policy that requires:
- 14-character passwords
- A mix of uppercase, lowercase, numbers, and symbols
- Password changes every 90 days
- No password reuse across accounts
Use a password manager (like LastPass or 1Password) to help employees generate and store complex passwords securely.
Enable Automatic Updates
Outdated software opens doors for cybercriminals. Configure all devices to automatically install updates for the operating system and all applications. This ensures prompt application of security patches.
Set a specific time for updates (preferably outside of working hours) to minimise disruption. For critical updates, use your MDM solution to push updates immediately.
Conduct Regular Security Audits
Proactive security measures prevent breaches. Schedule quarterly security audits to identify and address potential risks. These audits should include:
- Vulnerability scans of all devices
- Review of access logs
- Assessment of current security policies
- Evaluation of employee security awareness
Implement Remote Wiping Capabilities
Lost or stolen devices pose significant risks. Implement remote wiping capabilities through your MDM solution. This allows you to erase sensitive data from a device if it falls into the wrong hands.
Train employees on the importance of promptly reporting lost or stolen devices. Quick action can prevent data breaches and protect your company’s sensitive information.
Final Thoughts
Remote work security demands a comprehensive strategy. Companies must address unique challenges of distributed environments through VPNs, multi-factor authentication, and ongoing training. Effective device management, including mobile device management solutions and strong password policies, reduces data breach risks significantly.
The threat landscape evolves constantly. Businesses must stay informed about emerging threats and adapt their security measures. Regular policy reviews and proactive monitoring help companies maintain their edge over potential attackers.
Project IT specialises in securing remote workforces for New Zealand businesses. Our expert team assesses security postures, implements tailored solutions, and provides ongoing support (ensuring secure and efficient remote work setups). We understand the unique challenges faced by New Zealand businesses and offer comprehensive IT management and security solutions.


