Cloud security myths continue to circulate, causing unnecessary concern and hesitation among businesses considering cloud adoption. At Project IT, we’ve encountered numerous misconceptions that often hinder organisations from fully embracing the cloud’s potential.
In this post, we’ll tackle three common cloud security myths head-on, providing you with facts and insights to make informed decisions about your IT infrastructure.
Is Cloud Really Less Secure Than On-Premises?
The Shared Responsibility Model
Cloud security operates on a shared responsibility model. Cloud providers secure the infrastructure. Customers manage data security and access. This division allows each party to focus on their strengths.
Microsoft Azure captured nearly 25% of the global cloud market while growing revenue by 33% in Q1 2025. Their dedicated teams work around the clock to protect the underlying infrastructure. This level of investment and expertise is hard for most organisations to match in-house.
Advanced Security Measures
Cloud providers invest heavily in state-of-the-art security measures that most individual businesses cannot match. These include:
- Multi-factor authentication
- Encryption at rest and in transit
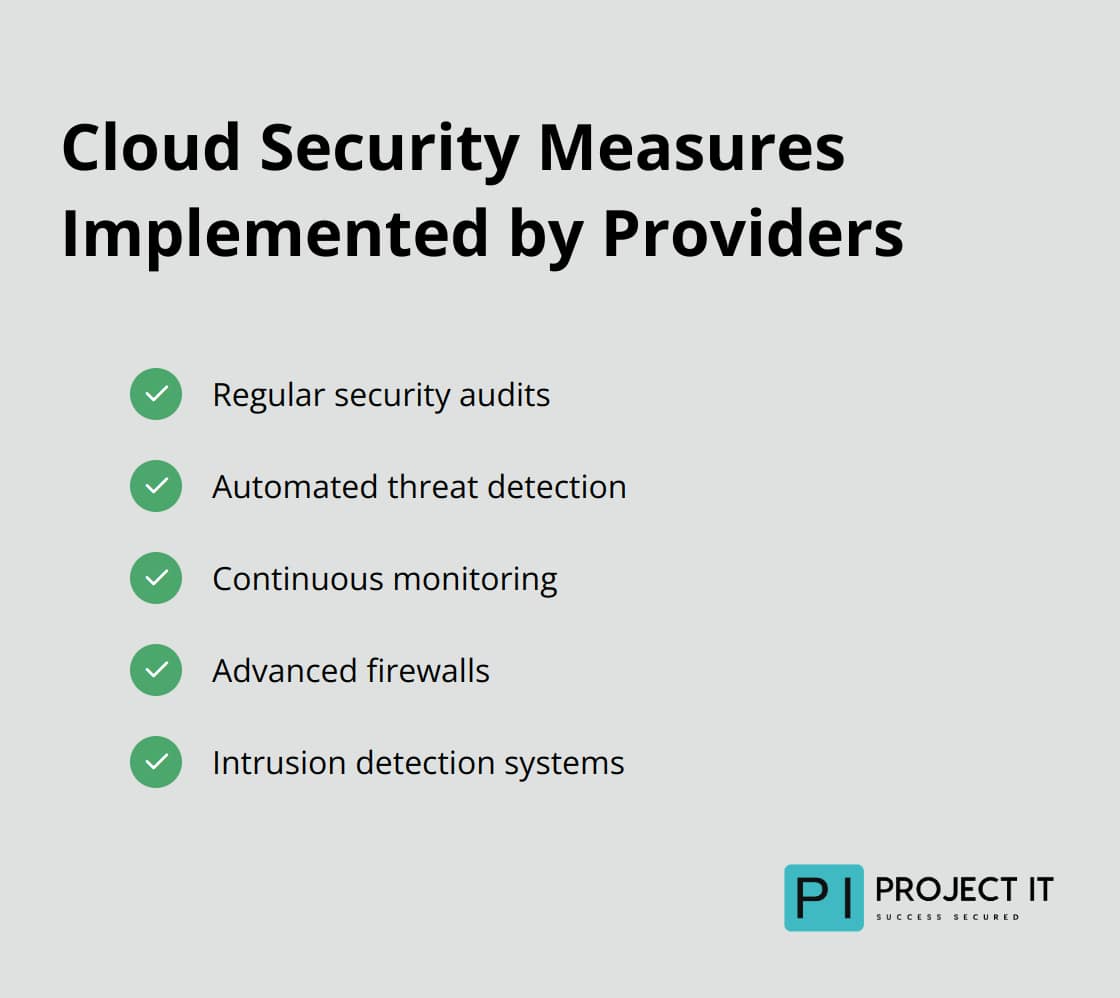
- Regular security audits
- Automated threat detection
- Continuous monitoring
These features are often included in standard cloud packages. For on-premises solutions, implementing similar measures can be costly and complex.
Security Incident Comparison
Data shows that cloud environments often fare better in security incidents. According to the Verizon 2023 Data Breach Investigations Report, the report investigated 16,312 security incidents, with 5,199 confirmed breaches. 83% involved external actors, 74% the human element, and 95% were financially motivated.
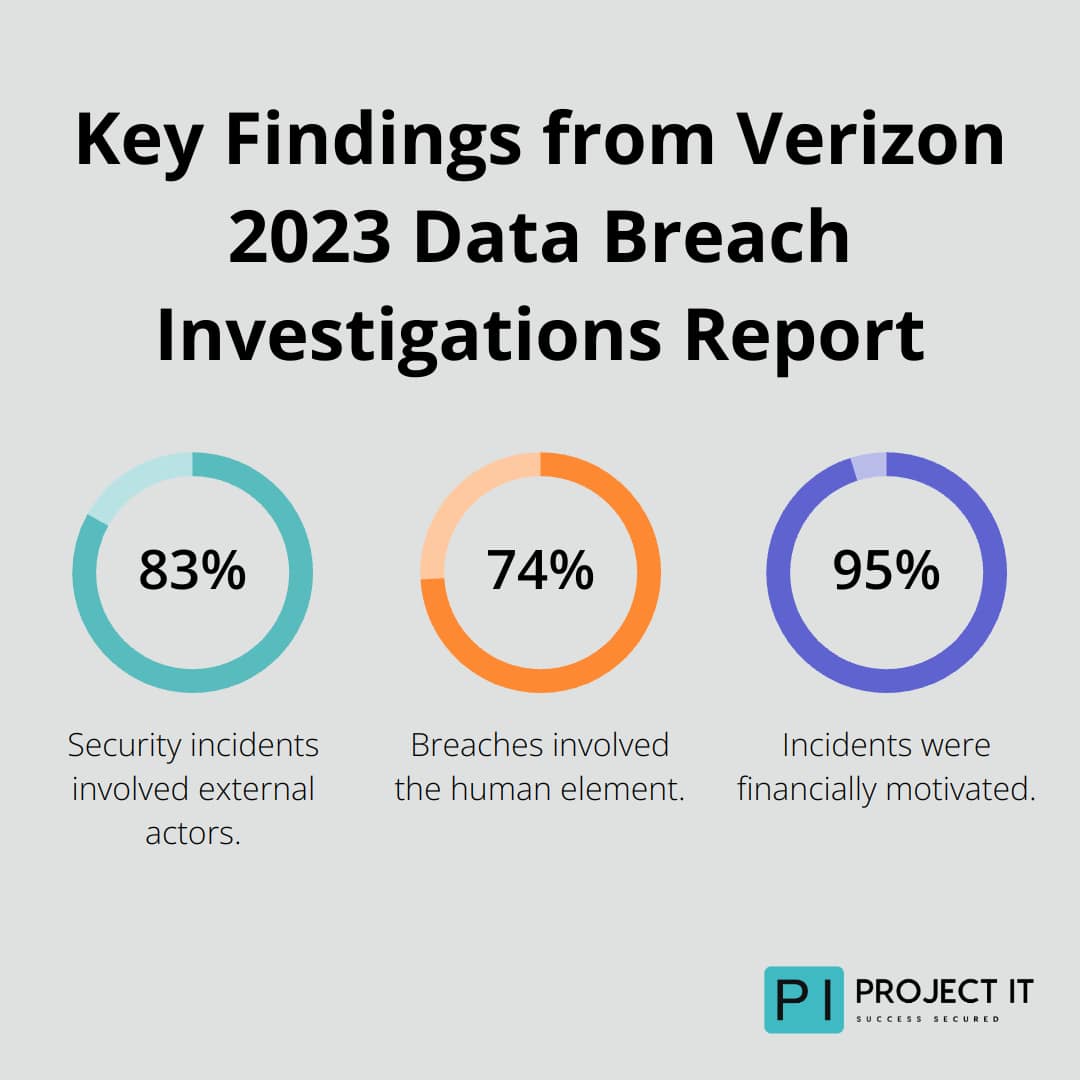
In contrast, on-premises environments accounted for 36% of breaches. This suggests that cloud environments, when properly configured, can be more resilient to attacks.
The Human Factor
Many security incidents stem from human error. Cloud providers offer tools to mitigate these risks. For instance, Azure provides Security Centre, which helps identify misconfigurations and suggests remediation steps.
On-premises environments often lack these automated safeguards. This can lead to overlooked vulnerabilities and increased risk.
Myth vs. Reality
The belief that on-premises solutions are inherently more secure persists despite evidence to the contrary. In reality, cloud adoption can strengthen security postures. Organisations can often achieve a higher level of security than with traditional on-premises solutions by leveraging cloud security features and following best practices.
As we move forward, it’s important to address another common misconception: the idea that data in the cloud is accessible to everyone. Let’s examine how cloud providers protect your data and ensure its privacy.
Is Your Cloud Data Really Secure?
Cloud security remains a top concern for businesses considering migration. Many worry about data accessibility in the cloud. Let’s address this myth head-on.
Strong Encryption Protects Your Data
Cloud providers use advanced encryption methods to safeguard your information. For example, Microsoft Azure uses AES-256 encryption for data at rest and TLS protocols for data in transit. This level of protection makes it extremely difficult for unauthorised parties to access your data.
The Cloud Security Alliance outlines cloud security best practices that have been developed to protect data in the cloud. Their guidance emphasizes the importance of encryption as a critical component of cloud security strategies.
Access Control Limits Data Exposure
Role-based access control (RBAC) and multi-factor authentication (MFA) are powerful tools in cloud security. RBAC ensures that users only have access to the data they need for their specific roles. MFA adds an extra layer of security by requiring multiple forms of verification before granting access.
Gartner reports that cybersecurity trends for 2025 reflect the need for more focused cybersecurity programmes that emphasize business continuity and collaborative risk management. Implementing strong access controls like RBAC and MFA aligns with these trends.
Data Isolation Keeps Your Information Separate
Cloud providers use sophisticated data isolation techniques to keep your information separate from other clients. This includes virtual private clouds, network segmentation, and containerisation.
Amazon Web Services (AWS) reports that their data isolation practices have resulted in zero breaches due to cross-tenant data access in the past five years. This demonstrates the effectiveness of these measures when properly implemented.
Real-World Security Measures
In practice, cloud data can be more secure than on-premises solutions when proper measures are in place. The key is to understand and implement these security features correctly. With the right approach, your data in the cloud can be just as secure-if not more so-than data stored on local servers.
Cloud providers often invest heavily in security measures that many individual businesses find challenging to match. These include (but are not limited to):
Now that we’ve addressed the myth of data accessibility in the cloud, let’s turn our attention to another common misconception: the idea that cloud security is too complex for small businesses to manage effectively.
Can Small Businesses Handle Cloud Security?
User-Friendly Tools Level the Playing Field
Cloud providers have created intuitive security tools. Microsoft’s Azure Security Centre offers a user-friendly dashboard that non-technical staff can navigate. It provides real-time security alerts and actionable recommendations, which enables small businesses to maintain a strong security posture.
A recent survey by Flexera found that more than a quarter of respondents spend over $12 million annually on cloud services. This significant investment has pushed the development of more accessible security solutions tailored for SMBs.
Managed Security Services: Your Virtual Security Team
For small businesses without dedicated IT staff, managed security services offer a cost-effective solution. These services provide expert monitoring, threat detection, and incident response 24/7.
A study by Kaspersky revealed that 98% of cybersecurity experts seek improvements to maximise protection. This highlights the importance of managed security services, which allow SMBs to benefit from enterprise-grade security without the overhead of a full-time security team.
Cost-Effective Solutions for Tight Budgets
Cloud security doesn’t require breaking the bank. Many providers offer tiered pricing models that allow small businesses to start with basic security features and scale up as needed. For example, AWS provides a free tier for its GuardDuty threat detection service, which allows SMBs to test advanced security features without upfront costs.
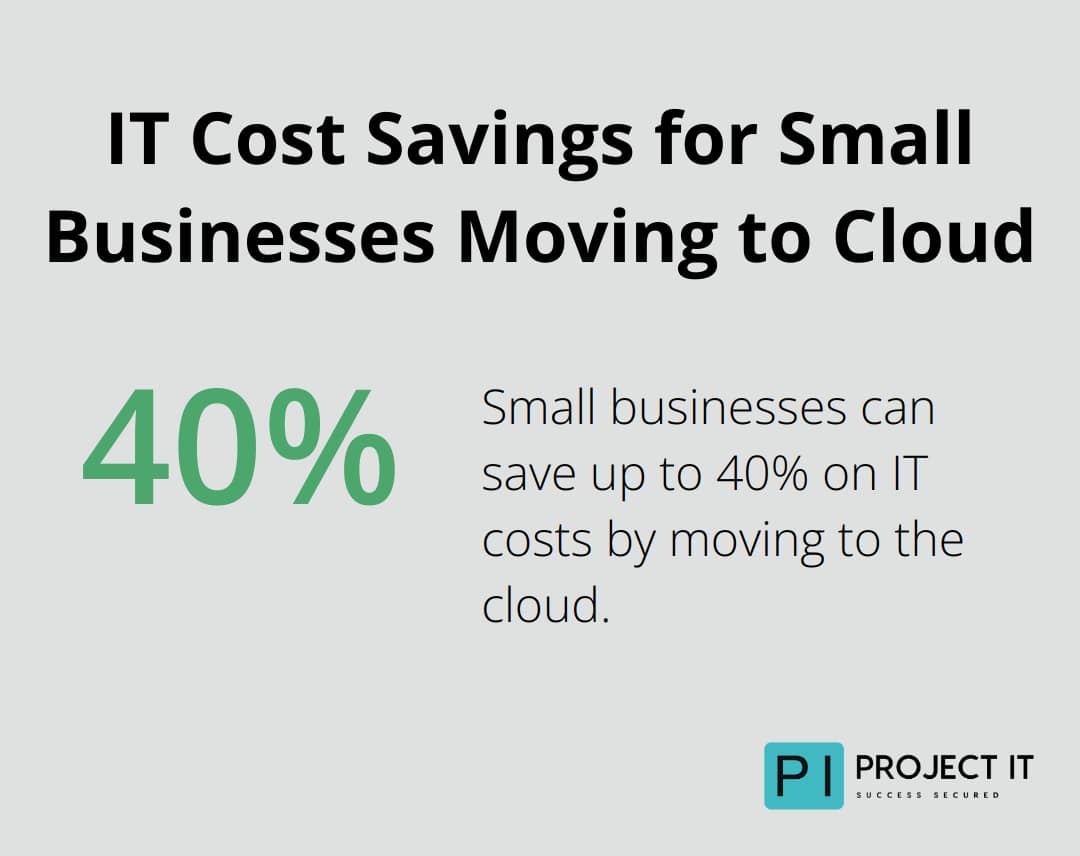
Cloud security often proves more cost-effective than traditional on-premises solutions. A report by Deloitte found that small businesses can save up to 40% on IT costs (including security expenses) by moving to the cloud.
Real-World Implementation
Small businesses can implement robust cloud security measures within their budget constraints. The right tools and services enable SMBs to achieve a level of security that was once only attainable for large enterprises.
Cloud security solutions (such as Microsoft Defender for Cloud and AWS GuardDuty) offer features like:
- Automated threat detection
- Compliance management
- Vulnerability assessments
- Security posture management
These tools help small businesses protect their data and systems without requiring extensive technical expertise.
Final Thoughts
This post debunked three common cloud security myths. We showed that cloud environments can offer stronger security than on-premises solutions when properly configured. The shared responsibility model and advanced features from cloud providers contribute to a robust security posture. Cloud security also protects data through encryption, access controls, and isolation techniques.
Small businesses can implement effective cloud security measures. User-friendly tools and cost-effective solutions make it possible for organisations of all sizes to enhance their security. Cloud security offers scalability and flexibility that can significantly improve an organisation’s overall protection against threats.
We at Project IT specialize in helping businesses navigate cloud security complexities. Our team can implement tailored security measures for your specific needs. Don’t let misconceptions prevent you from harnessing the full potential of cloud technology for your business.


